Issues » HTML Injection Error on Password Reset Login Page
| Issue: |
|
|---|---|
| Date: |
|
| Severity: | Medium |
| Requires Admin Access: | No |
| Fix Version: | 24.05.31 / 23.01.18 LTS / 23.10.24v11 LTS / 24.04.24v3 LTS |
| Credit: | Zakaria Agharghar |
| Description: |
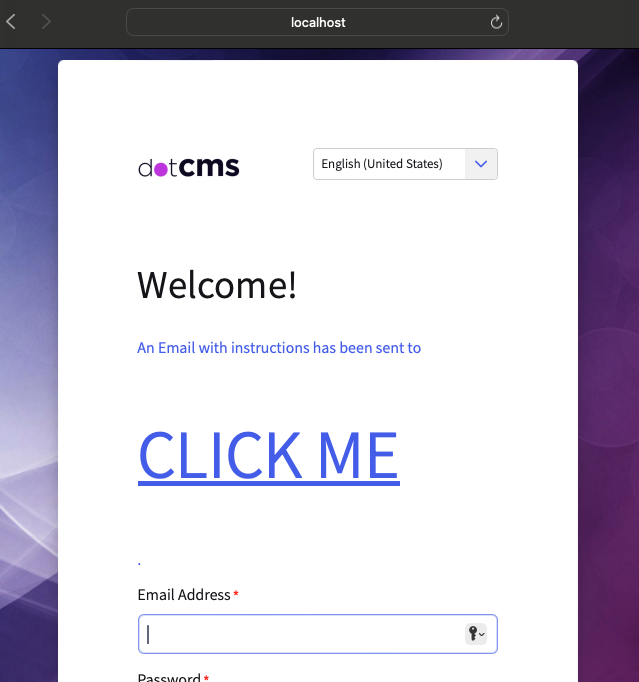
The "reset password" login page accepted an HTML injection via URL parameters. This has already been rectified via patch, and as such it cannot be demonstrated via Demo site link. Those interested to see the vulnerability may spin up a past docker image (prior to dotCMS 24.05.31) and use a link in the following fashion to on their local instance: http://localhost:8082/dotAdmin/#/public/login?resetEmailSent=true&resetEmail=%3Ch1%3E%3Ca%20href%3D%22https:%2F%2Fgoogle.com%22%3ECLICK%20ME%3C%2Fa%3E%3C%2Fh1%3E This will result in a view along these lines:
|
| Mitigation: |
Update to fix version or later. |
| References |
|